Wanna Cry Virus Patch Download
Download localized language security updates: Windows Server 2003 SP2 x64, Windows Server 2003 SP2 x86, Windows XP SP2 x64, Windows XP SP3 x86, Windows XP Embedded SP3 x86, Windows 8 x86, Windows 8 x64. How to enable and disable SMB in Windows and Windows Server & GPO deployment. DOWNLOAD Windows Security Update for WannaCry Ransomware (KB4012598) 1.0.0.0 for Windows top alternatives FREE Avira Antivir Virus Definitions for Avira 10 and Older.
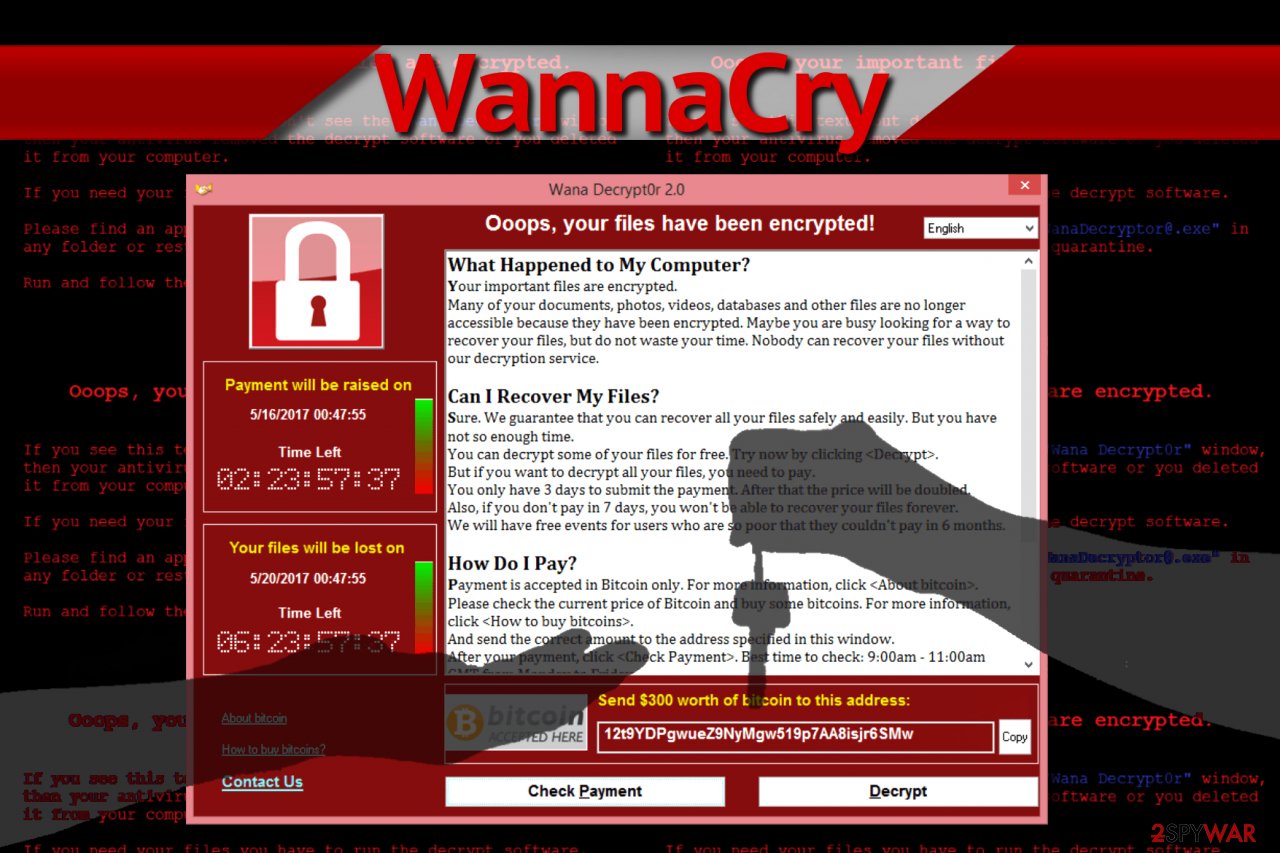
A global ransomware campaign, called WannaCry, has now infected over 10,000 organizations and 200,000 individuals in over 150 countries, including the UK National Health System which saw ambulances divert from affected hospitals. After a killer switch was activated by a security research simply registering a domain that stopped the original ransomware, new variants of the WannaCry started emerging.
The ransomware was developed to exploit the vulnerability in SMB used in a Windows-based network environment. Because of that, Linux, Mac OS are not affected by this widely spread ransomware. Windows 10 Creators Update computers are also not affected by WannaCry since the operating system already has this vulnerability patched up out of the box.

So, how to protect yourself from WannaCry Ransomware
1. Install the patch that Microsoft has released back in March to block the specific exploit that WannaCry is using. See more details below.
2. Update your anti-virus software definition. Most AV vendors have now added detection capability to block WannaCry.
3. If you don’t have any anti-virus software installed, you should consider install or enable Windows Defender (Security Essentials) which is free.
4. Backup, backup and backup. One of the fundamental defense against ransomware is the ability to reliably restore from backup.
What patch do I need for my machine?
The patch was released in March, namely Microsoft Security Bulletin MS17-010, which addresses the vulnerability that these attacks are exploiting. Basically, you can get your computer patched up through either Windows Update or install manually through Microsoft Update Catalog. Microsoft also made an exception and released security patches for their legacy operating systems such as Windows XP, Vista, and Windows Server 2003. You can find all individual patches and download them from Microsoft Update Catalog website.
If you have Windows Update set up to install updates automatically, your computer is most likely already patched up. But how do I now if that’s the case?
You can go to “View update history” in Windows Update in Control Panel to find out. Here are the list of KB numbers for this patch on various Windows systems.
- Windows Vista & Windows Server 2008: KB4012598
- Windows 7 & Windows Server 2008 R2: KB4012212 (Security Only) or KB4012215 (Monthly Rollup)
- Windows 8.1: KB4012213 (Security Only) or KB4012216 (Monthly Rollup)
- Windows Server 2012: KB4012214 (Security Only) or KB4012217 (Monthly Rollup)
- Windows Server 2012 R2: KB4012213 (Security Only) or KB4012216 (Monthly Rollup)
- Windows 10
- First release: KB4012606
- Version 1511: KB4013198
- Version 1607: KB4013429
- Windows 2016: KB4013429
Wanna Cry Virus Patch
What if I can’t patch my computer at the moment?
Well, you should consider disabling the vulnerable SMBv1 on all unpatched computers.
Wanna Cry Virus Patch Download Link
To disable SMBv1 on Windows 7, Windows Server 2008, Windows Server 2008 R2, Windows 8, and Windows Server 2012
To remove SMBv1 in Windows 2012 R2, and Windows Server 2016
Open Server Manager and launch Remove Roles and Features Wizard to remove SMB 1.0/CIFS File Sharing Support feature.
To remove SMBv1 from Windows 8.1 and Windows 10 computers
Open Control Panel and Turn Windows features on or off, and turn off SMB 1.0/CIFS File Sharing Support from the list.
Lastly, for further reading, Microsoft has released customer guidance for the WannaCry attacks and Troy Hunt has done an excellent detailed write-up on the WannaCry ransomware.
Related Posts
Hmm…maybe try the one listed in the following link: